All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutions










Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsProducts
Solutions
All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutionsIntegrations

Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsResources
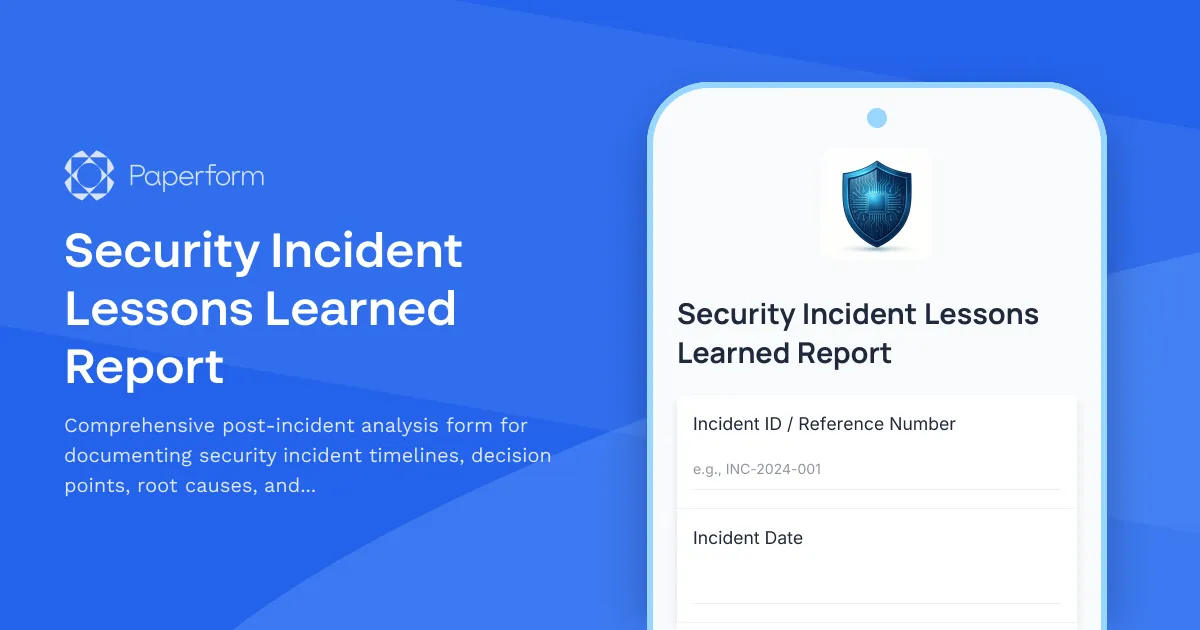
Security Incident Lessons Learned Report Template
Every security incident—whether it's a data breach, ransomware attack, insider threat, or system compromise—offers valuable insights that can strengthen your organization's cybersecurity posture. This Security Incident Lessons Learned Report template helps IT security teams, SOC analysts, and incident response managers capture critical details, reconstruct timelines, analyze decision points, and identify actionable process improvements after every incident.
Why Post-Incident Documentation Matters
In the chaos following a security event, it's easy to move straight into remediation and forget to document what actually happened. But without a structured lessons learned process, organizations risk repeating the same mistakes, missing opportunities to improve detection capabilities, and failing to close gaps in their incident response procedures.
This template ensures your team captures the full story—from initial detection through containment, eradication, and recovery—while the details are still fresh. By systematically analyzing what went well, what didn't, and where processes broke down, you can transform every incident into a learning opportunity that makes your security program stronger.
Built for Security Teams and IT Professionals
Whether you're a CISO, security analyst, incident response team lead, IT manager, or compliance officer, this form provides the structure you need to conduct thorough post-incident reviews. It's designed for organizations of all sizes—from lean security teams at SMBs to dedicated SOC operations at larger enterprises.
The form guides responders through critical documentation areas including incident classification, timeline reconstruction, root cause analysis, stakeholder communication effectiveness, and concrete remediation recommendations. Rather than relying on scattered notes and email threads, you'll have a single, comprehensive record that can be shared with leadership, compliance teams, and used to refine your incident response playbook.
Key Features of This Lessons Learned Template
Incident Overview & Classification: Capture essential incident metadata including incident ID, severity level, incident type (malware, phishing, DDoS, unauthorized access, etc.), systems affected, and the team members who responded. This context is crucial for trend analysis and future reference.
Detailed Timeline Reconstruction: Build a chronological record of the incident from initial detection through full resolution. Document when the incident was first detected, how it was discovered, containment actions, escalation points, and when normal operations resumed. This timeline becomes invaluable for understanding attack progression and identifying detection gaps.
Decision Point Analysis: Examine key decisions made during the response—which proved effective and which could be improved. This reflective analysis helps teams understand whether they followed documented procedures, made judgment calls based on incomplete information, or needed to improvise when playbooks fell short.
Root Cause Analysis: Go beyond surface-level symptoms to identify the underlying vulnerabilities, misconfigurations, process gaps, or human factors that allowed the incident to occur. Understanding root causes is essential for preventing recurrence.
Stakeholder Communication Review: Evaluate how effectively the team communicated with internal stakeholders, external partners, customers, and regulators. Clear communication during incidents is often as critical as technical response.
Process Improvement Tracking: Document specific, actionable recommendations for improving detection capabilities, response procedures, tools, training, and preventive controls. Assign owners and target completion dates to ensure improvements actually get implemented.
How Paperform Streamlines Incident Documentation
Rather than wrestling with generic survey tools or static PDF templates, this Paperform template provides a structured yet flexible documentation framework that actually works for security teams:
- Conditional logic shows relevant follow-up questions based on incident type and severity, so responders aren't overwhelmed with irrelevant fields
- Multi-page layout breaks the documentation into logical sections, making it easier to complete thorough reviews without form fatigue
- File upload fields let teams attach screenshots, log files, SIEM exports, network diagrams, and other evidence directly to the report
- Rich text formatting allows for detailed narrative descriptions of complex technical issues
- Automatic timestamping creates an audit trail of when documentation was completed
Once submitted, responses can automatically flow into your incident management system via Stepper (stepper.io), populate your security documentation repository, or trigger follow-up workflows for implementing recommended improvements.
Close the Loop on Incident Response
The most mature security programs don't just respond to incidents—they systematically learn from them. This template helps you close the loop on your incident response lifecycle, ensuring every security event contributes to organizational resilience rather than just becoming another closed ticket.
Use it after every significant security incident to build institutional knowledge, identify patterns across multiple events, demonstrate due diligence to auditors and regulators, and continuously refine your security operations.
Integration with Your Security Stack
Paperform integrates seamlessly with the tools security teams already rely on. Send completed lessons learned reports to Jira, ServiceNow, or other ticketing systems to track remediation tasks. Log findings in Notion or Confluence for your security documentation hub. Notify your Slack security channel when critical post-incident reviews are completed. Or use Stepper to automatically create follow-up tasks, schedule review meetings, and ensure accountability for process improvements.
For organizations with compliance requirements around incident documentation (SOC 2, ISO 27001, PCI DSS, HIPAA), this structured template provides auditable evidence of your lessons learned process, demonstrating continuous improvement in your security program.
Getting Started
Whether you're documenting a minor security event or conducting a major incident post-mortem, this template adapts to your needs. Customize sections based on your organization's incident classification framework, add custom fields for specific compliance requirements, or integrate with your existing incident response playbook.
Security incidents are inevitable—but repeating the same mistakes isn't. Start building a more resilient security program by systematically capturing and acting on lessons learned from every incident.
Ready to strengthen your incident response? Use this template to turn security incidents into opportunities for growth, and empower your team with the insights needed to prevent, detect, and respond to future threats more effectively.