All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutions










Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsProducts
Solutions
All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutionsIntegrations

Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsResources
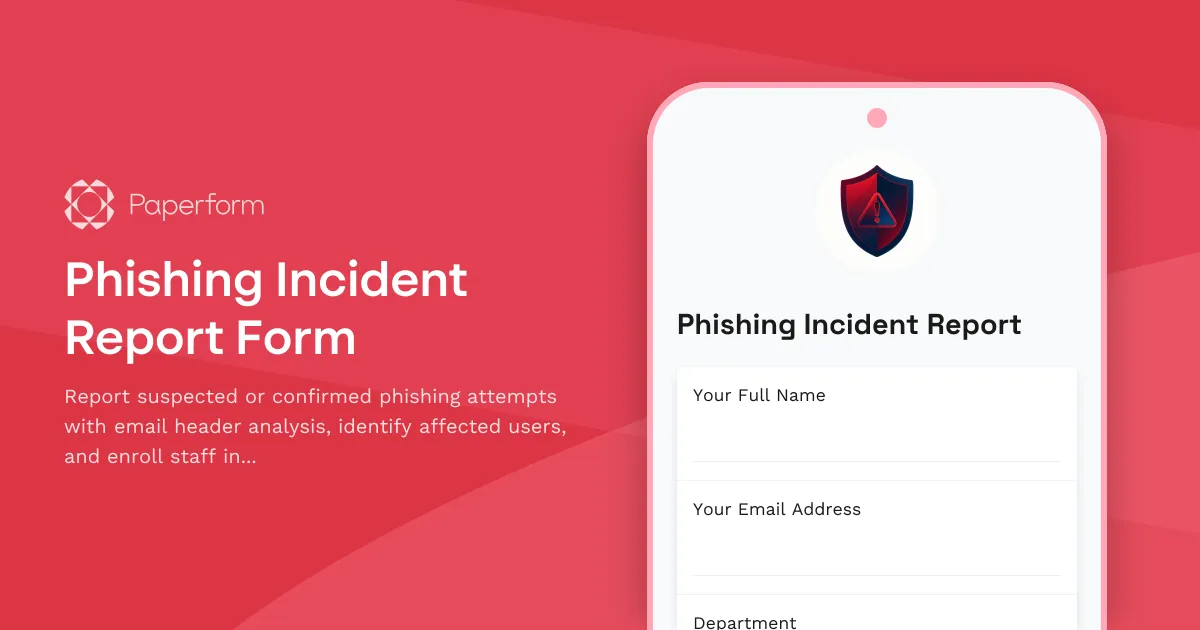
When a phishing email slips through your defenses, speed and detail matter. This Phishing Incident Report Form gives IT and security teams a structured way to capture critical information—email headers, sender details, affected users and incident context—so you can investigate, contain and respond faster.
Built for IT managers, security officers, compliance teams and help desk staff, this template is designed to streamline your incident response workflow. Instead of chasing down details over Slack or parsing forwarded emails, you collect everything you need in one submission: full email headers for forensic analysis, user impact assessment, and the option to immediately enroll affected employees in security awareness training.
Why Paperform works for phishing response
Phishing incidents require fast triage and clear documentation. With Paperform's conditional logic, you can show or hide follow-up questions based on severity, route high-priority reports to your SOC or IT lead, and trigger alerts in Slack or Microsoft Teams the moment a critical submission arrives.
Connect this form to your ticketing system (Jira, ServiceNow, Freshdesk) via Stepper to auto-create incidents, tag them by threat type, and kick off investigation workflows without manual data entry. You can also sync reports to Google Sheets or Airtable for trend analysis, and use Paperform's AI Insights to surface patterns across multiple phishing campaigns—like common sender domains, targeted departments, or recurring social engineering tactics.
For organizations that need an audit trail, every submission is timestamped, stored securely (SOC 2 Type II compliant), and exportable for compliance reporting or post-incident reviews.
Security awareness training, built in
One of the biggest wins from a phishing report isn't just stopping the threat—it's preventing the next one. This template includes an opt-in (or required) enrollment question for security awareness training, so you can immediately flag users who need refresher courses and feed that list into your LMS, HR system or training calendar via Stepper automation.
Whether you're a lean IT team at a growing SaaS company or a security operations center managing hundreds of endpoints, this form gives you the structure, speed and automation to turn phishing reports into actionable intelligence—and a more security-aware workforce.