All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutions










Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsProducts
Solutions
All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutionsIntegrations

Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsResources
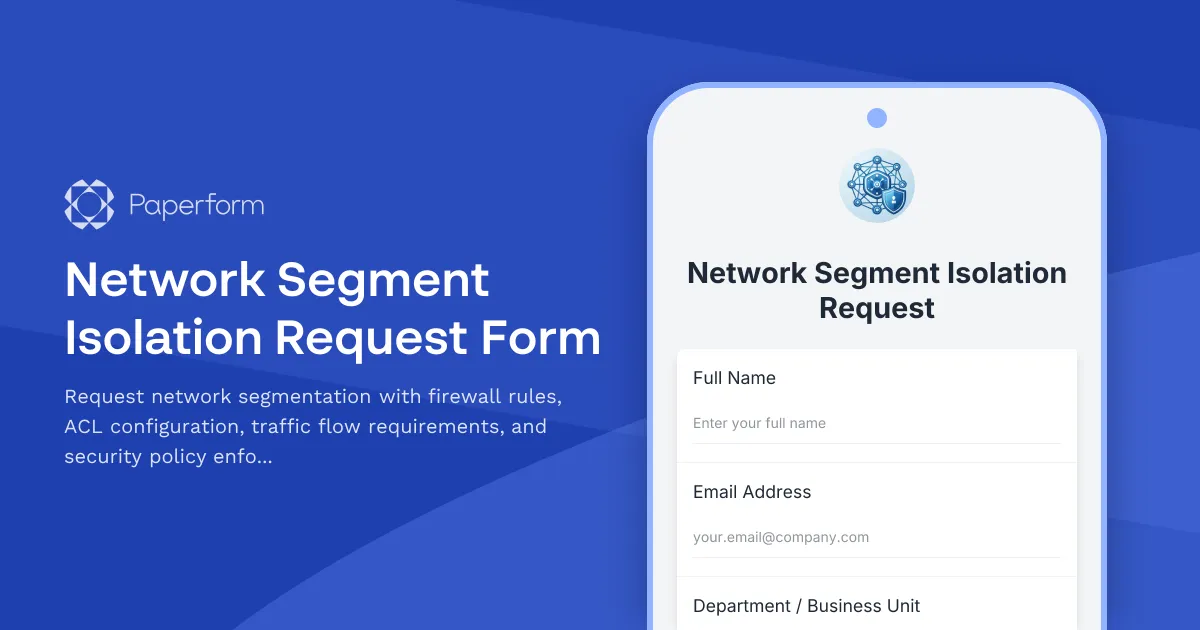
Secure Your Infrastructure with Network Segment Isolation
Network segmentation is a critical security control for modern IT infrastructure. Whether you're isolating production from development environments, creating secure zones for sensitive data, or implementing zero-trust architecture, a well-structured network segment isolation request process ensures changes are properly reviewed, documented, and implemented without disrupting business operations.
Why Use This Network Segment Isolation Request Template?
This template streamlines the process of requesting network segmentation changes, from defining firewall rules and ACLs to documenting traffic flow requirements and security policies. IT teams can capture all the technical details needed to implement changes safely, while maintaining a clear audit trail for compliance and security reviews.
Key features of this template:
- Comprehensive technical capture – Collect network segment details, IP ranges, VLAN configurations, and routing requirements in a structured format
- Firewall rule management – Document inbound and outbound firewall rules with protocols, ports, source/destination criteria, and business justification
- ACL configuration – Specify access control list requirements for granular traffic control
- Traffic flow mapping – Define expected communication patterns, service dependencies, and data flow between segments
- Security policy enforcement – Ensure isolation requests align with organizational security standards and compliance requirements
- Impact assessment – Evaluate potential effects on existing services, applications, and user access
- Approval workflow – Route requests through security, network, and management teams for proper oversight
Who This Template Is For
This network segment isolation request form is designed for IT professionals managing enterprise infrastructure, including:
- IT managers and operations teams submitting segmentation requests for new projects or security improvements
- Security engineers implementing zero-trust architecture, microsegmentation, or compliance-driven isolation
- Network administrators processing firewall changes, ACL updates, and routing modifications
- DevOps teams requesting isolated environments for development, staging, and production workloads
- System architects designing secure multi-tier application architectures
- Compliance officers ensuring network controls meet regulatory requirements
Streamline Network Security with Paperform and Stepper
Paperform makes it simple to create professional IT request forms that capture complex technical requirements without overwhelming requesters. The clean, guided interface helps IT teams collect accurate information upfront, reducing back-and-forth and speeding up implementation.
When a network isolation request is submitted, Stepper can automatically orchestrate your approval and implementation workflow:
- Route requests to the appropriate security and network teams based on risk level or environment type
- Create tickets in your ITSM platform (ServiceNow, Jira Service Management, etc.) with all technical details populated
- Send approval requests to network security managers and infrastructure leads
- Update your CMDB or network documentation tools with new segment configurations
- Notify stakeholders when changes are scheduled, implemented, or complete
- Log all changes in your audit system for compliance tracking
This automation eliminates manual handoffs, ensures consistent process adherence, and maintains complete visibility throughout the request lifecycle.
Built for IT Teams That Value Security and Efficiency
Network segmentation is a powerful security control, but it requires careful planning and coordination. With this template, you can:
- Reduce security risks by ensuring all isolation requests include proper justification and security review
- Maintain compliance with detailed documentation of firewall rules, ACLs, and policy enforcement
- Prevent service disruptions by mapping traffic flows and dependencies before implementation
- Accelerate approvals with clear, complete technical specifications in every request
- Create audit trails for security reviews, compliance audits, and incident investigations
Paperform is trusted by IT teams worldwide for its flexibility, security, and ease of use. With SOC 2 Type II compliance, SSO support, and enterprise-grade features, you can confidently manage sensitive infrastructure requests.
Ready to Strengthen Your Network Security?
Start using this network segment isolation request template to bring structure, security, and efficiency to your network segmentation process. Whether you're implementing microsegmentation, isolating sensitive workloads, or enforcing zero-trust principles, Paperform gives you the tools to manage complex IT requests with confidence.