All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutions










Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsProducts
Solutions
All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutionsIntegrations

Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsResources
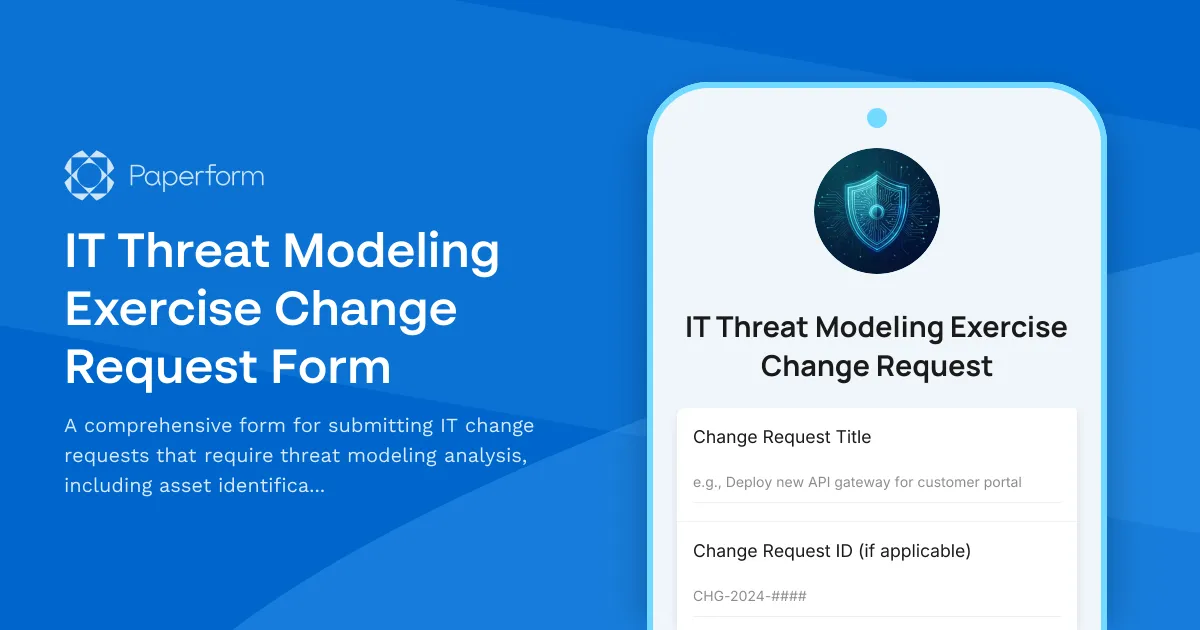
IT Threat Modeling Exercise Change Request Form
When implementing significant IT changes—whether deploying new infrastructure, modifying security architecture, or rolling out new applications—understanding potential threats before they become vulnerabilities is critical. This IT threat modeling exercise change request form provides IT teams, security professionals, and system administrators with a structured approach to identifying assets, analyzing threat scenarios, and defining mitigation controls before changes go live.
Why threat modeling matters for IT change management
Traditional change request forms focus on what's changing and when. But for changes that touch critical systems, customer data, or security infrastructure, you also need to understand what could go wrong. Threat modeling helps IT and security teams systematically identify potential attack vectors, assess risk exposure, and build appropriate controls into the change from the start—reducing the likelihood of post-deployment incidents, compliance violations, or emergency rollbacks.
This template guides requesters through the entire threat modeling exercise: documenting the proposed change, cataloging affected assets and data flows, identifying realistic threat scenarios (from insider threats to external attacks), assessing likelihood and impact, and defining concrete mitigation controls. It's designed for mid-sized IT teams, managed service providers, and security-conscious organizations that want to embed proactive risk assessment into their change approval workflows.
How Paperform streamlines threat modeling and change approvals
Built on Paperform, this form goes beyond static PDFs or spreadsheet templates. You can embed conditional logic to show different threat scenario prompts based on the type of change (infrastructure, application, network, or data), use calculations to auto-score risk levels based on likelihood and impact ratings, and trigger approval workflows in tools like Jira, ServiceNow, or Slack using Stepper (stepper.io), Paperform's AI-native workflow automation platform.
Once a threat modeling request is submitted, Stepper can route high-risk changes to your security team for review, send medium-risk changes directly to the CAB (Change Advisory Board) for scheduling, and auto-approve low-risk changes with predefined controls. You can also log all submissions to Airtable, Google Sheets, or your ITSM platform, keeping a complete audit trail of every threat assessment tied to each change request.
Who this form is for
This template is ideal for:
- IT managers and system administrators overseeing infrastructure, application, and network changes
- Security teams and CISOs embedding threat modeling into the SDLC and change management lifecycle
- DevOps and platform engineers deploying new services or modifying cloud architecture
- MSPs and IT consultants managing change controls for multiple clients under security frameworks like ISO 27001, NIST, or SOC 2
- Compliance and risk teams ensuring changes are assessed for data protection, regulatory, and operational risk
Whether you're implementing a new API gateway, migrating to a zero-trust network model, or rolling out a third-party integration, this form ensures every significant change is evaluated through a security lens—before it reaches production.
Key features
- Asset and data flow identification to understand what's at risk
- Threat scenario library covering common attack vectors like privilege escalation, data exfiltration, denial of service, and supply chain compromise
- Risk scoring matrix with likelihood and impact ratings to prioritize mitigation efforts
- Mitigation control documentation including preventive, detective, and corrective measures
- Conditional workflows to route high-risk changes for additional review and approval
- Audit-ready records for compliance reporting and post-incident analysis
Start using this threat modeling change request form today and bring proactive security assessment into every IT change—reducing risk, improving resilience, and building a culture of security-first thinking across your organization.