All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutions










Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsProducts
Solutions
All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutionsIntegrations

Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsResources
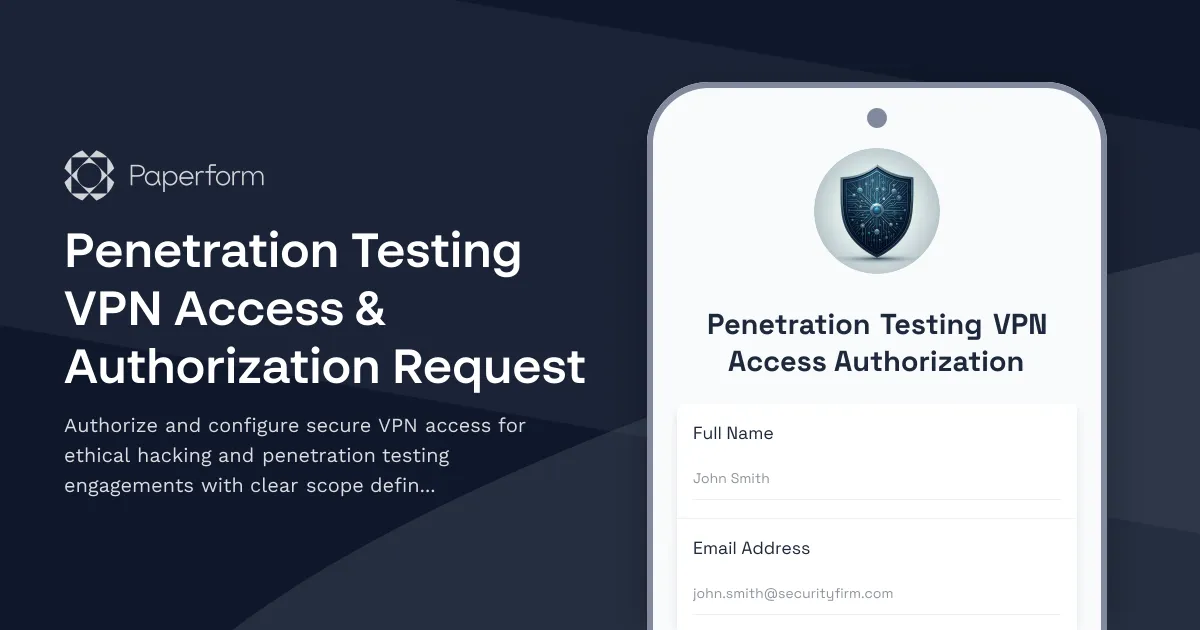
Secure Your Penetration Testing Engagements with Professional Authorization
For cybersecurity firms conducting penetration tests, establishing clear authorization and secure access is non-negotiable. This Penetration Testing VPN Access & Authorization Request template helps you formalize ethical hacking engagements with proper documentation, scope definition, and legal protection—all in one streamlined form.
Why Paperform for Penetration Testing Authorization?
Cybersecurity professionals need tools that match their security standards. This template helps penetration testers, security consultants, and IT security teams establish authorized access to client systems while maintaining comprehensive documentation trails. With Paperform's SOC 2 Type II compliance and robust security features, you can confidently manage sensitive authorization workflows.
The form captures essential details including engagement scope, target systems, IP ranges, testing methodologies, and explicit authorization from stakeholders. By collecting structured data upfront, you reduce legal risk, prevent scope creep, and ensure everyone understands exactly what will be tested and when.
Streamline Your Security Workflow with Automation
Once a penetration tester submits their access request, you need fast turnaround. Connect this form to Stepper, Paperform's AI-native workflow builder, to automatically:
- Route authorization requests to the appropriate security officer or client stakeholder
- Generate VPN credentials and send secure access details via encrypted channels
- Update your project management system with engagement details and timelines
- Create audit logs in your compliance documentation system
- Trigger automatic calendar invites for testing windows and debriefs
You can also integrate with security tools like Jira, Slack, Google Workspace, or your ticketing system to keep your security operations center informed in real-time.
Protect Your Business with Formal Authorization
Penetration testing without explicit written authorization isn't ethical hacking—it's illegal. This template includes clear authorization language, scope limitations, and acknowledgment fields that protect both your firm and your clients. Use Papersign to automatically convert completed forms into legally binding authorization agreements with eSignatures from client stakeholders, creating an unbreakable chain of custody for your compliance records.
Whether you're an independent penetration tester, part of a cybersecurity consultancy, or managing an internal red team, this template provides the professional structure you need to conduct authorized security assessments confidently and compliantly.