All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutions










Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsProducts
Solutions
All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutionsIntegrations

Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsResources
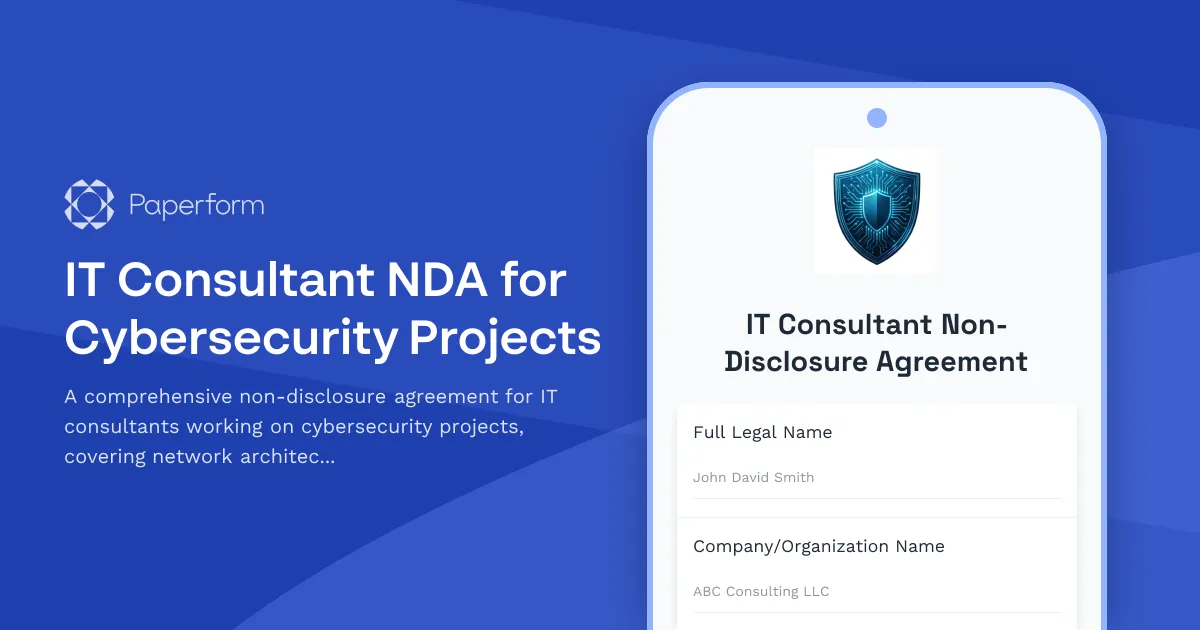
Protect Your Cybersecurity Assets with a Purpose-Built NDA
When you're bringing external IT consultants into sensitive cybersecurity projects, standard NDAs often fall short. Network architecture diagrams, penetration test results, vulnerability assessments, and security infrastructure details represent some of your organization's most valuable—and vulnerable—intellectual property.
This IT Consultant NDA template is specifically designed for cybersecurity engagements where confidentiality isn't just a legal formality, it's mission-critical. Whether you're hiring consultants for security audits, network redesigns, incident response, or compliance assessments, this template ensures all parties understand exactly what information must remain confidential and the consequences of disclosure.
Built for IT Security & Consulting Firms
This template addresses the unique confidentiality requirements of cybersecurity work. It covers protection of network architecture documentation, penetration testing methodologies and findings, security vulnerabilities, access credentials, incident response procedures, and proprietary security tools. The agreement also includes security clearance verification fields to ensure consultants meet the necessary background and certification requirements before accessing sensitive systems.
Paperform makes it easy to collect consultant details, verify credentials, outline specific project parameters, and capture legally binding eSignatures—all in one professional, branded form. Once submitted, you can use Papersign to route the signed agreement through internal approval workflows and generate fully executed copies for all parties, creating a complete audit trail that's essential for compliance and risk management.
For firms managing multiple consultant engagements, Stepper can automate your entire onboarding workflow: when a consultant signs the NDA, automatically create a folder in your document management system, notify your IT security team, provision temporary credentials with appropriate access levels, and add the consultant to your compliance tracking system—all without manual handoffs.
Who This Template Is For
This form is ideal for cybersecurity firms, IT consulting agencies, managed service providers (MSPs), enterprise IT departments, compliance officers, and legal teams who regularly engage external consultants for security-sensitive projects. It's particularly valuable for organizations in regulated industries (finance, healthcare, government contracting) where data breaches or unauthorized disclosure can result in significant legal, financial, and reputational damage.
With Paperform's SOC 2 Type II compliance and robust security features, you can confidently collect sensitive information about projects, clearances, and confidential systems knowing that your intake process meets the same high standards you apply to the rest of your security infrastructure.