All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutions










Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsProducts
Solutions
All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutionsIntegrations

Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsResources
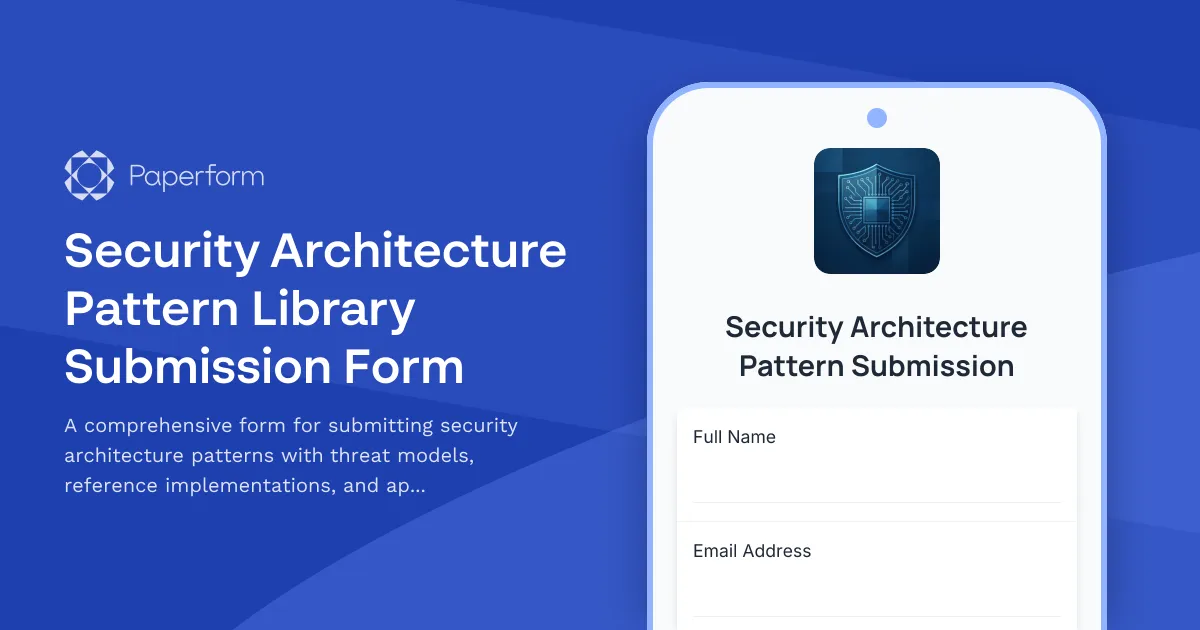
Build a Robust Security Architecture Pattern Library
Security architecture patterns are the foundation of consistent, scalable security across your organization. This Security Architecture Pattern Library Submission Form streamlines the process of documenting, reviewing, and approving new patterns for your enterprise architecture team.
Whether you're an IT security architect, DevSecOps engineer, or infrastructure lead, this template helps you capture every critical detail—from threat models and attack vectors to reference implementations and approved technology stacks—in a structured, standardized format.
What You Can Do With This Template
- Document security patterns systematically with clear descriptions, use cases, and security objectives
- Capture comprehensive threat models including STRIDE analysis, attack vectors, and mitigation strategies
- Link reference implementations with code repositories, diagrams, and deployment guides
- Track approved technology stacks and component dependencies for consistent tooling
- Enable security review workflows that route submissions to the right stakeholders
- Maintain compliance requirements and regulatory mappings for each pattern
Perfect for IT Security Teams
This form is designed for organizations that take security architecture seriously. IT security teams, cloud architects, and DevSecOps professionals can use it to build a centralized pattern library that promotes reusable security solutions, reduces risk, and accelerates secure development.
Paperform's conditional logic lets you show or hide fields based on pattern type, sensitivity level, or compliance requirements. Embed the form on your internal wiki, share it with your architecture review board, or integrate it directly into your governance workflows.
Automate Your Security Workflow
Connect this form to your existing tools using Stepper, Paperform's AI-native workflow builder. Automatically route submissions to security architects for review, create tickets in Jira or ServiceNow, update your architecture repository in Confluence or Notion, and notify stakeholders when patterns are approved—all without writing a single line of code.
With Paperform's SOC 2 Type II compliance, SSO support, and role-based permissions, you can confidently manage sensitive security documentation while maintaining audit trails and access controls your enterprise requires.