All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutions










Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsProducts
Solutions
All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutionsIntegrations

Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsResources
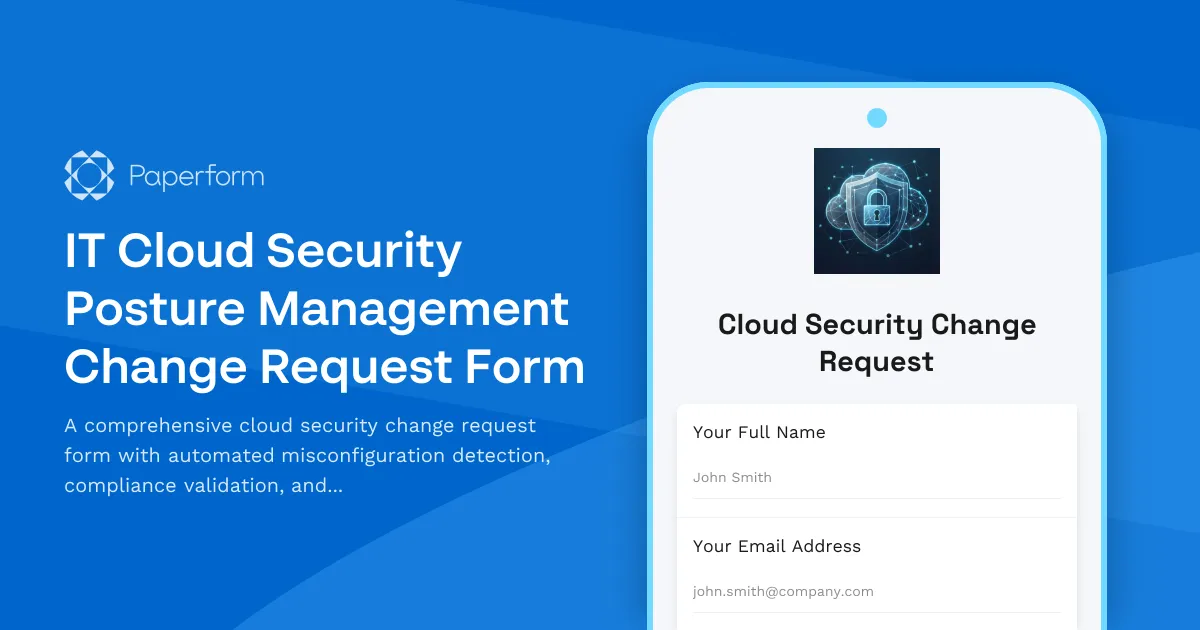
Streamline Cloud Security Changes with Automated Compliance Checks
Managing cloud security posture across AWS, Azure, Google Cloud, and hybrid environments requires careful change control and continuous compliance monitoring. This IT Cloud Security Posture Management (CSPM) Change Request Form gives IT security teams, DevOps engineers, and compliance officers a structured way to request, review, and approve cloud security changes while automatically detecting misconfigurations and triggering remediation workflows.
Whether you're updating firewall rules, modifying IAM policies, adjusting encryption settings, or reconfiguring cloud resources, this form ensures every change is documented, risk-assessed, and validated against your security frameworks—including CIS Benchmarks, SOC 2, ISO 27001, PCI DSS, and HIPAA.
Built for IT security teams managing cloud infrastructure
This template is designed for organizations that need rigorous change control for cloud security configurations. Typical users include security operations centers (SOCs), cloud infrastructure teams, DevOps engineers, and IT managers responsible for maintaining security posture across multi-cloud and hybrid environments.
The form captures essential details like the affected cloud platform, resource type, change category, business justification, and risk assessment—then routes approvals based on risk level and triggers automated compliance checks before implementation.
Automated compliance validation and remediation triggers
Once a cloud security change request is submitted, you can use Stepper to automate the entire approval and validation workflow. Connect your CSPM tools (Wiz, Prisma Cloud, Lacework, Orca Security), infrastructure-as-code scanners (Checkov, Terrascan), and ticketing systems (Jira, ServiceNow) to automatically:
- Run compliance scans against CIS, NIST, and industry frameworks
- Detect policy violations and misconfigurations before deployment
- Route high-risk changes to security architects for manual review
- Trigger remediation playbooks for common security issues
- Update CMDB and audit logs with change records
- Send real-time notifications to Slack or Microsoft Teams
This automation reduces manual review time, prevents security drift, and ensures every change is compliant before it reaches production.
Designed for technical teams with clear workflows
The form uses conditional logic to adapt based on the type of change requested—network security changes reveal firewall rule fields, IAM changes show permission scope options, and encryption changes capture key management details. This keeps the form relevant and prevents teams from filling out unnecessary fields.
Risk assessment questions help categorize changes as low, medium, high, or critical, automatically determining approval workflows and compliance requirements. Rollback plans and testing evidence fields ensure teams have thought through implementation and recovery scenarios before submitting.
Paperform makes cloud security governance scalable
For IT teams managing security across distributed cloud environments, Paperform provides the flexibility to build compliance-aware forms that integrate with your existing security stack. With Papersign, you can turn approved change requests into formal sign-off documents for audit trails. With Stepper, you can orchestrate the entire change management lifecycle—from submission through approval, implementation, validation, and documentation—all triggered by a single form submission.
Whether you're a small security team managing a single cloud provider or an enterprise SOC overseeing multi-cloud infrastructure, this template gives you a professional, auditable starting point that can scale with your security governance needs.