All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutions










Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsProducts
Solutions
All Solutions

Explore all the solutions you can create with Paperform: surveys, quizzes, tests, payment forms, scheduling forms, and a whole lot more.
See all solutionsIntegrations

Connect with over 2,000 popular apps and software to improve productivity and automate workflows
See all integrationsResources
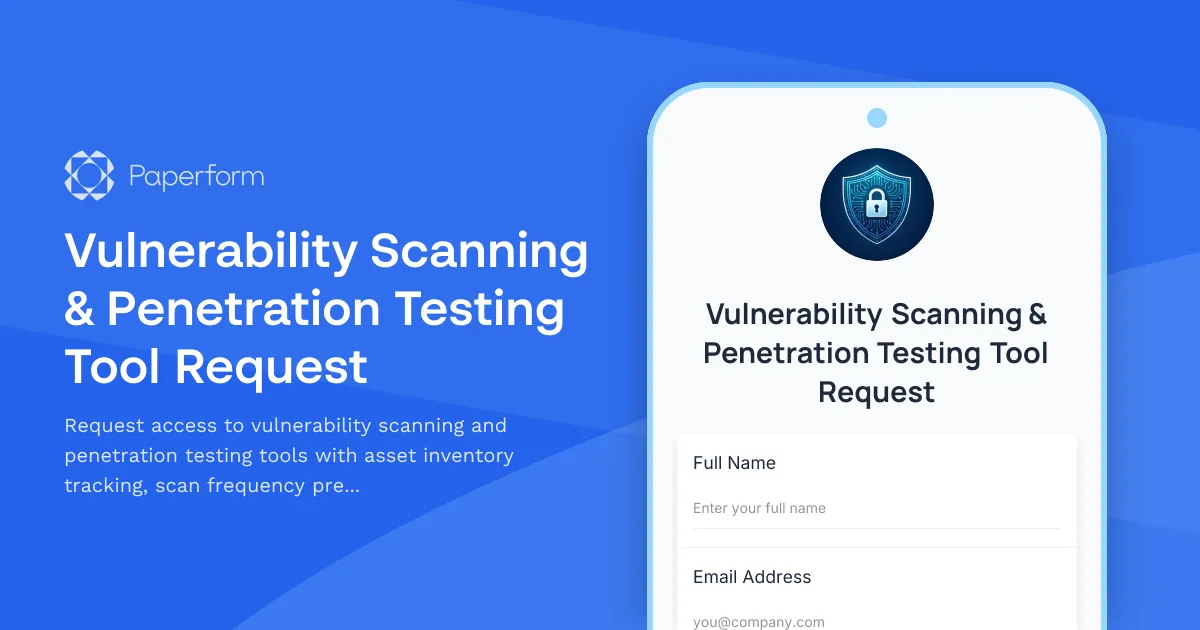
Streamline Your Security Tool Requests with Paperform
Managing cybersecurity tools and access across your IT infrastructure shouldn't involve endless email threads and manual spreadsheets. This Vulnerability Scanning & Penetration Testing Tool Request template helps IT teams, security analysts, and compliance officers efficiently request, document, and track security testing tools while maintaining comprehensive asset inventories and remediation workflows.
Built for IT Security Teams
Whether you're an IT Manager, Security Analyst, or Compliance Officer, this template captures everything you need for proper security tool provisioning: asset details, scan frequencies, compliance framework requirements, and remediation tracking preferences. The structured format ensures nothing gets missed while speeding up approval workflows.
Automate Your Security Workflows with Stepper
Once a tool request is submitted through Paperform, you can use Stepper to automatically route approvals to security leads, provision access in your identity management system, update your CMDB or asset register, and trigger onboarding documentation. This creates a seamless, auditable trail from request to deployment—essential for SOC 2, ISO 27001, and other compliance frameworks.
Why IT Professionals Choose Paperform
Paperform's conditional logic adapts the form based on tool type, compliance requirements, and asset scope. Integration with Slack, Jira, ServiceNow, and other IT tools means requests flow directly into your existing ticketing and project management systems. With SOC 2 Type II compliance, role-based permissions, and data residency controls, Paperform meets the security standards IT teams demand.
Start streamlining your vulnerability scanning and penetration testing tool requests today—no coding required, just a professional form that works as hard as your security team does.